Encapsulation theory: the transformation equations of absolute information hiding.
Edmund Kirwan*
Abstract
This paper describes how the potential coupling of an encapsulated set varies as the set is transformed, that is, as elements are added and removed. The equations governing the changes caused by these transformations are derived and briefly analysed.
Keywords
Encapsulation theory, encapsulation, potential coupling, transformation equation.
1. Introduction
The potential coupling of an encapsulated set was introduced in [1], which derived the equations for the potential coupling of any given set of absolute information hiding. These equations, however, were static, offering no insight into the evolution of a set over time.
This paper addresses this evolutionary aspect by deriving the equations which describe not the overall potential coupling of a set but the changes in potential coupling as a set undergoes an arbitrary series of transformations.
This paper considers sets of absolute information hiding only.
2. Standard deviation
Before examining the transformation equations themselves, let us preform some experiments whose results we shall compare with those we might intuitively expect.
Proposition 1.11 in [1] showed that, given two otherwise equivalent encapsulated sets, both of which uniformly distributed in violational elements, the set whose information-hidden elements are non-uniformly distributed over disjoint primary sets can never have a potential coupling of less than that of the set with uniformly distributed information-hidden elements.
This may be understood qualitatively by considering the internal potential coupling of a disjoint primary set which, as also shown in [1], was shown to be proportional to the square of the number of elements in that disjoint primary set. Thus consider a set of uniformly distributed elements where each disjoint primary set has 10 elements; each disjoint primary set will have an internal potential coupling of 90 (=102 - 10). An element moved from one disjoint primary set to another will (in a sense we shall later define precisely) increase the, "Non-evenness," of the distribution: now one disjoint primary set will have 11 elements and an internal potential coupling of 110 (=112 - 11), whereas the donor disjoint primary set will have an internal potential coupling of 72 (=92 - 9): moving this element has caused an overall internal potential coupling increase of 2.
Loosely speaking, being proportional to the square of the number of elements in a disjoint primary set, the internal potential coupling tends to amplify deviations from uniform distribution, so the more non-uniformly distributed a set is, the greater its potential coupling.
Can we investigate this relationship more formally? Can we rigorously measure this, "Unevenness?"
Indeed we can, by using a tool of the statistician: the standard deviation. The standard deviation measures how widely spread the values in a dataset are. We shall use it first to measure how widely spread the number of information-hidden elements per disjoint primary set is, that is, to measure the hidden element distribution.
If we take an encapsulated
set of r disjoint primary sets where xi
is the number of hidden elements in the ith
disjoint primary set and where![]() is
the average number of hidden elements per disjoint primary set, then
the standard deviation is defined by the equation:
is
the average number of hidden elements per disjoint primary set, then
the standard deviation is defined by the equation:
![]()
The standard deviation of the hidden element distribution for a uniformly distributed set is 0; this figure then rises as the set becomes increasingly non-uniformly distributed.
Instead of examining how the potential coupling behaves as the standard deviation of the hidden element distribution increases, however, it is useful to instead examine how the isoledensal configuration efficiency (also defined in [1]) behaves, as the configuration efficiency, being defined between 0 and 1, helps to normalise the trend for sets of different cardinalities. Thus, whereas we expect that the potential coupling of a set will rise as the standard deviation of its hidden element distribution increases, we expect the configuration efficiency of that set to fall as its standard deviation increases.
Finally, we need only state the actual means of increasing the non-uniformity of an encapsulated set's distribution. We shall begin not with a perfectly uniformly distributed set but with a set of, say, 100 disjoint primary sets, each disjoint primary set having one violational element, and a random number - between 0 and 30 - of information-hidden elements.
Being non-uniformly distributed the encapsulated set will have a non-zero standard deviation of hidden element distribution. We shall then take one hidden element from a disjoint primary set and move it to an arbitrarily designated target disjoint primary set. We shall record the change in the hidden element distribution standard deviation and its resulting change in configuration efficiency. We shall then move a second hidden element from a disjoint primary set into the target disjoint primary set and perform the measurement again. This shall be repeated until all the hidden elements of the set are in the target disjoint primary set, thus maximising the hidden element distribution standard deviation.
Figure 1 shows the resulting configuration efficiency plotted as a function of the changing hidden element distribution standard deviation.
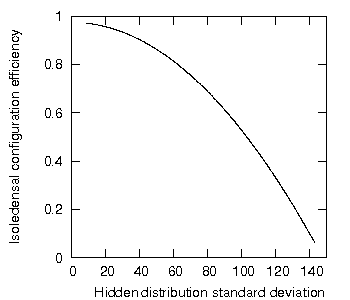
Figure 1: Isoledensal configuration efficiency as a function of increasing standard deviation of the hidden element distribution.
This figure shows the expected result: the isoledensal configuration efficiency falls as the hidden element distribution standard deviation increases, i.e., as the encapsulated set becomes increasingly non-uniformly distributed in hidden elements.
To show a slightly broader example of this trend, Figure 2 shows a further ten randomly-generated sets subjected to the same experiment.
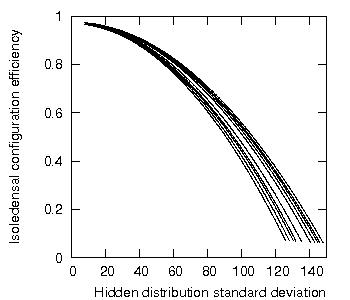
Figure 2: Isoledensal configuration efficiency as a function of increasing standard deviation, multiple sets.
We shall now examine the five transformation equations and attempt to confirm the above results in terms of the appropriate equation.
3. The transformation equations
From the point of view of investigating changes in potential coupling there are only two fundamental transformations we can make to any encapsulated set: we can add a given number of violational elements to a disjoint primary set and we can add a given number of information-hidden elements to a disjoint primary set. Let us denote this, "Given number," m.
It may seem that we could also transform an encapsulated set by adding a disjoint primary set itself, but in encapsulation theory dependencies can only be formed between elements, not disjoint primary sets, and so adding any number of empty disjoint primary sets cannot change the potential coupling of that encapsulated set. Of course, by definition, no element can exist outside a disjoint primary set, so these transformations therefore presume, where necessary, the existence of an empty disjoint primary set into which new elements may be introduced.
Although only two transformations are fundamental, it is possible to derive a further three transformations from these two fundamental transformations. These three derived transformations both cover common changes to sets and yield insight into the nature of the changing potential coupling The three derived transformations are: moving m violational elements from one disjoint primary set to another, moving m information-hidden elements from one disjoint primary set to another, and converting m information-hidden elements in a disjoint primary set into m violational elements.
We note that m may be
negative and we establish the convention that adding a negative
number of elements to a disjoint primary set may be interpreted as
removing![]() elements
from that disjoint primary set. Where m is negative, it may
not exceed the number of elements that actually reside within a
disjoint primary set: no disjoint primary set may contain a negative
number of elements at any time.
elements
from that disjoint primary set. Where m is negative, it may
not exceed the number of elements that actually reside within a
disjoint primary set: no disjoint primary set may contain a negative
number of elements at any time.
Before proceeding, we recall the definitions of the terms from [1]:
![]() :
an encapsulated set.
:
an encapsulated set.
![]() :
The number of violational elements in encapsulated
set G.
:
The number of violational elements in encapsulated
set G.
![]() :
disjoint primary sets in encapsulated
set G. Kx is used when only one
disjoint primary set is involved. Translation transformations involve
two disjoint primary sets: Ks is the source
disjoint primary set from which elements are moved, Kt
is the target disjoint primary set to which elements are moved.
:
disjoint primary sets in encapsulated
set G. Kx is used when only one
disjoint primary set is involved. Translation transformations involve
two disjoint primary sets: Ks is the source
disjoint primary set from which elements are moved, Kt
is the target disjoint primary set to which elements are moved.
![]() :
The total number of elements in disjoint primary set Kx.
:
The total number of elements in disjoint primary set Kx.
![]() :
The number of violational elements in disjoint primary set Kx.
:
The number of violational elements in disjoint primary set Kx.
![]() :
the total number of elements in an encapsulated
set.
:
the total number of elements in an encapsulated
set.
Finally, we introduce two
functions. The function![]() will
represent the change of potential coupling of encapsulated
set G due to the application of some transformation.
The function h(Kx) will represent the
number of information-hidden elements in disjoint primary set Kx.
will
represent the change of potential coupling of encapsulated
set G due to the application of some transformation.
The function h(Kx) will represent the
number of information-hidden elements in disjoint primary set Kx.
Box 1 lists the five transformation equations.
|
Box 1: The five transformation equations.
4. Reflections on the equations
4.1 The non-conservative transformation equations
Consider the first two transformation equations. These are the fundamental equations and they are non-conservative in that they change the total number of elements in the encapsulated set; the other three equations are conservative in that they do not change the total number of elements in the set.
Perhaps the most interesting aspect of the two non-conservative transformation equations is that it is trivial to show (by subtracting the second from the first) that adding a violational element to an encapsulated set causes a larger increase in potential coupling than adding a hidden element, as we intuitively expect.
4.2 The translation transformation equations
The third and fourth equations are derived from the first two. These equations are translation equations in that they show how potential coupling changes as elements are translated or moved from one disjoint primary set to another. We shall examine them in reverse order.
4.2.1 The fourth equation
Consider the fourth transformation equation, describing the change of potential coupling as information-hidden elements are moved between disjoint primary sets. This is the equation governing the changes that we found in section 2, where all the hidden elements of a set were incrementally translated from their original disjoint primary sets to a specific target disjoint primary set, thereby maximising the standard deviation of the hidden element distribution.
If we look at the terms of the fourth equation, we see that there are three components of the potential coupling change (ignoring the common scaling m factor):
(i)![]()
(ii)![]()
(iii)![]()
The 2m component is clearly independent of the disjoint primary sets affected by the transformation.
Component (i) is the difference in the total number of elements (multiplied by two) between the source and target disjoint primary sets.
Component (ii) is the difference in the number of violational elements between the source and target disjoint primary sets, though in the opposite sense of component (i) in that component (i) is target minus source but component (ii) is source minus target.
The interaction between these two components is complicated, but in our experiment in section 2, we moved more and more hidden elements into a single, target disjoint primary set, causing the target disjoint primary set to become increasingly large while its violational elements remained unchanged: thus component (i) grew to dominate component (ii) and repeated translations increasingly added to the potential coupling of the set. Increasing the potential coupling of a fixed number of elements by definition decreases the set's configuration efficiency and this is precisely figures 1 and 2 show.
The reverse is also true: moving information-hidden elements from a larger to a smaller disjoint primary set must necessarily decrease the potential coupling of a set and thus increase the configuration efficiency. This explains why a set of uniformly distributed hidden elements cannot have a potential coupling greater than one of non-uniformly distributed hidden elements (all else being equal).
4.2.2. The third equation
Whereas the fourth transformation moved information-hidden elements between disjoint primary sets, the third transformation moves violational elements between disjoint primary sets.
We might expect this equation to yield results quite similar to the fourth equation given that they are both translation transformations, but this is not the case. To investigate this curious difference we shall perform another experiment.
In section 2 we plotted the falling configuration efficiency of a set as its hidden elements were increasingly piled into just one disjoint primary set. Let us perform a similar experiment but this time we shall incrementally move only the violational elements into one disjoint primary set. (A minor difference in procedure must be observed: every disjoint primary set must contain at least one violational element as otherwise it is uncontactable by elements in other disjoint primary sets, so instead of moving all violational elements from the source disjoint primary sets, we shall move all but one violational element. This difference in itself should not significantly alter the outcome.)
Let us again take a set of 100 disjoint primary sets. In section 2 we put one violational element in each disjoint primary set and put a random number - between 0 and 30 - of information-hidden elements in each disjoint primary set. For our new experiment we shall do the opposite, putting one information-hidden element in each disjoint primary set and putting a random number - between 1 and 30 - of violational elements in each disjoint primary set.
In section 2, it was the standard deviation of the hidden element distribution that we measured; this time we shall measure the standard deviation of the violational element distribution: the number of violational elements per disjoint primary set. Incrementally moving one violational element into one target disjoint primary set will repeatedly increase the standard deviation of the violational element distribution of the entire set. The question is: how will the configuration efficiency change as the standard deviation of the violational element distribution increases? The result is shown in figure 3.
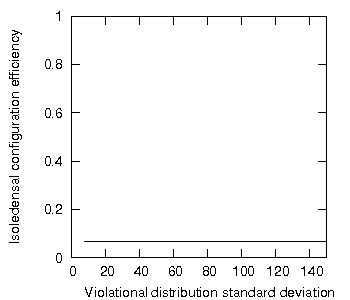
Figure 3: Isoledensal configuration efficiency as a function of increasing standard deviation of the violational element distribution.
Figure 3 reveals two aspects that call for explanation but only one is relevant here. Firstly, the low the configuration efficiency of this encapsulated set may be striking but this is simply due to the way we created the set. The set was created with just one hidden element in each disjoint primary set and up to 30 violational elements in each disjoint primary set; the set is therefore composed overwhelmingly of violational elements and as such exploits little encapsulation: hence the low configuration efficiency.
More relevant to our experiment and perhaps more surprising is the result that in our sample encapsulated set the configuration efficiency is independent of violational distribution standard deviation; in other words, the potential coupling of the set is unchanged by moving all the possible violational elements into one disjoint primary set.
Why is this result so different from the first experiment with information-hidden elements?
The answer lies in the third equation.
Let us again break the equation into its component parts; we see it is just the simple difference between two terms (ignoring the common scaling m factor) :
(i)
![]()
This is much easier to interpret than equation four. Component (i) is just the difference between the number of hidden elements of the target and source disjoint primary sets.
In our experiment all the disjoint primary sets have the same number of hidden elements, thus the difference between the number of hidden elements in any two disjoint primary sets is zero. So it doesn't matter how many violational elements are moved between disjoint primary sets: these translations cannot change the potential coupling and cannot change the configuration efficiency of the set. This explains the unchanging configuration efficiency of figure 3.
4.2.3. Non-uniformity
In both experiments performed so far, one set of elements was uniformly distributed: in the first experiment, each disjoint primary set had just one violational element whereas the hidden elements were non-uniformly distributed; in the second experiment, each disjoint primary set had one hidden element whereas the violational elements were non-uniformly distributed. To model more, "Real world," problems, we must examine encapsulated sets whose hidden elements and violational elements are both non-uniformly distributed.
Let us re-visit the first experiment and look at the translation of hidden elements in an encapsulated set again of 100 disjoint primary sets with each disjoint primary set having a random number - between 0 and 30 - of hidden elements and a random number - between 1 and 30 - of violational elements. Before we do so, however, we shall attempt to predict the results by examining the translation transformation equation for hidden elements, the fourth equation in box 1.
As we noted before, the dominant component of translation transformation equation for hidden elements is simply the total number of elements in the target minus the total number of elements in the source. As we are choosing at random the target disjoint primary set into which all the hidden elements will be moved, then this disjoint primary set will initially have between 0 and 60 elements in total (there will be at most 30 hidden and at most 30 violational elements).
It is therefore conceivable that the first source disjoint primary set chosen for a translation will have more elements than our target disjoint primary set, and so the total number of elements in the target disjoint primary set minus the total number of elements in the source disjoint primary set will be negative; this negative change in potential coupling implies that the configuration efficiency of the set would initially rise.
As more translations are performed, however, we should quickly reach a situation, in a randomly distributed set, where the number of hidden elements in the target disjoint primary set becomes greater than the number of elements in any other single disjoint primary set; this will certainly be the case when the target disjoint primary set contains 61 elements and will probably be the case much sooner. After this point, all the hidden element translations will increase the potential coupling and increase the standard deviation of the hidden element distribution. This will yield a picture very similar to that already shown in figure 1: the configuration efficiency will fall as the hidden element distribution standard deviation increases. The results are shown in figure 4.
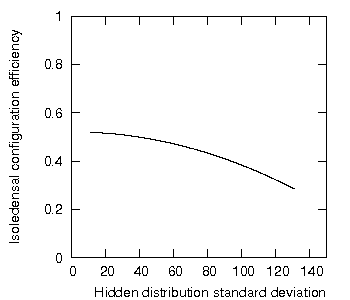
Figure 4: Isoledensal configuration efficiency as a function of increasing standard deviation of the hidden element distribution for an encapsulated set with non-uniformly distributed hidden and violational elements.
There are three aspects of figure 4 that require explanation but only two are relevant to our experiment.
Compared with figure 1, the initial configuration efficiency of the encapsulated set in figure 4 is rather low, but this is due to the set's now containing multiple hidden and multiple violational elements randomly distributed: any such set with a non-trivial number of disjoint primary sets will usually have a configuration efficiency of around 0.5. (Recall that the set in figure 1 had only one violational element per disjoint primary set: it was extremely well encapsulated and hence its configuration efficiency was much higher than our latest set.)
The second and most interesting aspect of figure 4 is that, as suspected, the configuration efficiency of an encapsulated set of non-uniformly distributed hidden and violational elements falls with increasing hidden element distribution standard deviation, just as was the case with the non-uniformly distributed hidden elements and uniformly distributed violational elements of the first experiment.
There only remains to be explained why the terminal configuration efficiency of the encapsulated set in figure 4 is not as low as that in figure 1. The explanation comes again from the fourth equation. The largest change of potential coupling occurs when the difference in total number of elements between the source and target disjoint primary sets is maximised. In our first experiment, all the disjoint primary sets contained only one violational element but in this latest experiment there were always a random number of violational elements left behind when the hidden elements were extracted, thus the differences in total number of elements between target and source disjoint primary sets were not as great as those in the first experiment which in turn causes the potential coupling to rise by a lesser amount than in the first experiment. This directly translates to the configuration efficiency's not falling as far in our latest experiment.
As before, merely to demonstrate the trend, figure 5 shows ten randomly generated encapsulated sets, each constrained as was the set in figure 4, subjected to repeated hidden translation transformations.
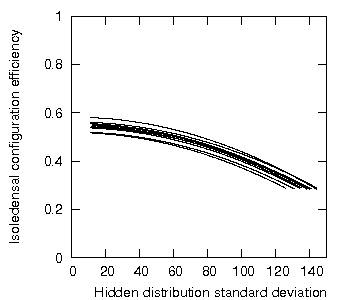
Figure 5: Isoledensal configuration efficiency as a function of increasing standard deviation of the hidden element distribution for a set with non-uniformly distributed hidden and violational elements, multiple sets.
Let us also re-visit the second experiment and look at the translation of violational elements in an encapsulated set again of 100 disjoint primary sets with each disjoint primary set having a random number - between 0 and 30 - of hidden elements and a random number - between 1 and 30 - of violational elements. Before we do so, however, we shall attempt to predict the results by examining the translation transformation equation for violational elements, the third equation in box 1.
As we saw, the equation showed us that the change in potential coupling generated by the translation depends only on the difference between the numbers of hidden elements in the target and source disjoint primary sets. In our previous violation translation experiment, that difference was zero, and so moving all the violational elements to one target disjoint primary set had no effect on the set's potential coupling or configuration efficiency.
In our randomly generated encapsulated set, however, the difference will usually be non-zero and so there will usually be a change of potential coupling It will not, however, resemble the potential coupling change caused by hidden element translations. In hidden element translations, the change in potential coupling was proportional to the difference of the number of elements in the target and source elements, and this change grew increasingly large as the target element grew increasingly large. The very act of translating a hidden element to the target disjoint primary set increased the change in potential coupling caused by translating all subsequent hidden elements to the target disjoint primary set.
The third equation exhibits very different behaviour. The change in potential coupling is proportional to the difference in the number of hidden elements only and moving violational elements does not change the number of hidden elements in source or target disjoint primary set. Thus repeated violational element translations will not generate potential coupling changes proportional to the increasing size of the target disjoint primary set: the change in potential coupling is fixed by the choice of source and target disjoint primary sets.
Also, suppose the target disjoint primary set has 15 hidden elements; then translating violational elements from a source disjoint primary set with fewer than 15 hidden elements will cause an increase of potential coupling and translating violational elements from a source disjoint primary set with more than 15 elements will cause a decrease of potential coupling So unlike the hidden element translations, which after an initial time were guaranteed to only increase potential coupling, violational element translations can lead to small increases of potential coupling which can then be offset by subsequent small decreases of potential coupling1
In other words, although the increasing violational distribution standard deviation will usually change the configuration efficiency, we do not expect configuration efficiency to change by anything like as much as was caused by the hidden element translations: the configuration efficiency should be quite insensitive to increasing violational distribution standard deviation.
The results of repeated violational element translations of a set non-uniformly distributed in both hidden and violational elements is shown in figure 6.
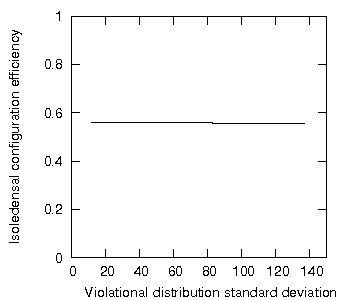
Figure 6: Isoledensal configuration efficiency as a function of increasing standard deviation of the violational element distribution for a set with non-uniformly distributed hidden and violational elements.
As figure 6 indeed shows, configuration efficiency does change with increasing violational distribution standard deviation, but only negligibly. Figure 7 shows the results for multiple randomly-generated sets.
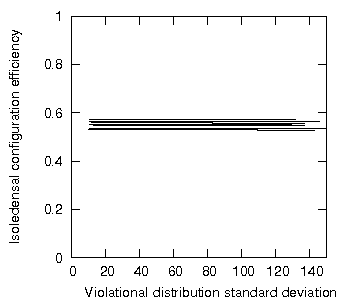
Figure 7: Isoledensal configuration efficiency as a function of increasing standard deviation of the violational element distribution for a set with non-uniformly distributed hidden and violational elements, multiple sets.
4.3.The fifth equation
The fifth equation in box 1 is the conversion transformation equation, which gives the change of potential coupling when m information-hidden elements are converted into violational elements. The equation simply states that when a hidden element in a disjoint primary set is converted into a violational element in that same disjoint primary set, then the potential coupling must rise. This just confirms our expectation that increasing the access to an element within a disjoint primary set must raise the potential coupling of a set. The reverse is also true: the change of potential coupling in converting a violational element to a hidden element can be calculated by changing the sign of the m, which then shows that such a conversion must reduce the potential coupling of a set.
5. Conclusions
Systems evolve. To control this evolution means be able to deterministically predict the affects of changes before those changes occur. For systems that can be modelled by sets, this primarily means predicting the potential coupling of the set before the changes occur. This paper proposed that the evolution of a set may be modelled as an arbitrarily complex series of transformations that may be applied to that set.
The two fundamental transformations were then established that describe all changes to a set and the two potential coupling equations corresponding to those transformations were proposed. Three further equations were derived from these fundamental equations to describe the more common changes that sets undergo.
6. Related work
-
7. Appendix A
7.1. Definitions
Note that in these
definitions the![]() symbol
means, "Maps to."
symbol
means, "Maps to."
[D3.1] Given
primary set Q with
disjoint primary set K in encapsulated set G and
the transformation T, the change of internal potential
coupling![]() effected
by applying T to Q
is given by equation:
effected
by applying T to Q
is given by equation:
![]()
The change of internal potential coupling![]() effected
by applying T to G is given by equation:
effected
by applying T to G is given by equation:
![]()
[D3.2]
Given primary set Q
with disjoint primary set K in
encapsulated set G and
the transformation T, the change of external potential
coupling![]() effected
by applying T to Q
is given by equation:
effected
by applying T to Q
is given by equation:
![]()
The change of external potential coupling![]() effected
by applying T to G is given by equation:
effected
by applying T to G is given by equation:
![]()
[D3.3]
Given primary set Q with disjoint primary set K in
encapsulated set G and the transformation T, the change
of potential coupling![]() effected
by applying T to Q is given by equation:
effected
by applying T to Q is given by equation:
![]()
The
change of potential coupling![]() effected
by applying T to G is given by equation:
effected
by applying T to G is given by equation:
![]()
[D3.4] Given the
encapsulated set G with an
ith
disjoint primary set Ki
of
![]() elements and external information-hiding violation of v(Ki),
let Tp
be the violational transformation which maps Ki
onto Ki*
where Ki*
differs from Ki
by m violational
elements where
elements and external information-hiding violation of v(Ki),
let Tp
be the violational transformation which maps Ki
onto Ki*
where Ki*
differs from Ki
by m violational
elements where![]() or:
or:
![]()
Where Tp is applied to just the xth disjoint primary set Kx of G, the transformation becomes:
![]()
And:
![]()
Note that as m may be positive or negative, Ki* may have more or fewer violational elements than Ki.
[D3.5]
Given the encapsulated set G with an
ith
disjoint primary set Ki
of
![]() elements and external information-hiding violation of v(Ki),
let Tz
be the hidden transformation which maps Ki
onto Ki*
where Ki*
differs from Ki
by m
information-hidden elements where
elements and external information-hiding violation of v(Ki),
let Tz
be the hidden transformation which maps Ki
onto Ki*
where Ki*
differs from Ki
by m
information-hidden elements where![]() and
where the violational elements remain unchanged, that is:
and
where the violational elements remain unchanged, that is:
![]()
Where Tz is applied to just the xth disjoint primary set Kx of G, the transformation becomes:
![]()
Note that as m may be positive or negative, Ki* may have more or fewer information-hidden elements than Ki.
[D3.6]
The information-hiding function of encapsulated set G, written h(G),
is the function that maps the information-hidden elements of that set
to their own set. The information-hiding of set G is the
cardinality of its information-hiding function,![]() .
The information-hiding of disjoint primary set K is the
cardinality of its information-hiding function,
.
The information-hiding of disjoint primary set K is the
cardinality of its information-hiding function,![]() .
The information-hiding of G divided by the number of disjoint
primary sets is called the specific information-hiding of G.
Given that a set consists entirely of information-hidden and
violational elements, then by definition:
.
The information-hiding of G divided by the number of disjoint
primary sets is called the specific information-hiding of G.
Given that a set consists entirely of information-hidden and
violational elements, then by definition:
(i)![]()
(ii)
![]()
7.2. Propositions
The propositions are organised as follows.
Propositions 3.1 - 3.5 establish some general results concerning the sum of changes of potential coupling and the application of transformations to sets.
Propositions 3.6 - 3.11 establish the fundamental transformation equation for the application of the violational transformation to a set.
Propositions 3.12 - 3.17 establish the fundamental transformation equation for the application of the hidden transformation to a set.
Propositions 3.18 - 3.20 establish the three derived transformation equations for the translation and conversion transformations.
All propositions relate to sets of absolute information-hiding only.
Proposition 3.1.
Given
the encapsulated set G and
the transformation T,
the change of potential coupling![]() effected
by applying T to G
is given by:
effected
by applying T to G
is given by:
![]()
Proof:
By proposition 1.3.17 in [1]:
![]() (i)
(i)
Let K* = T(K). Therefore:
![]() (ii)
(ii)
Also be definition:
![]() (iii)
(iii)
Substituting (i) and (ii) into (iii) gives:
![]()
=![]()
=![]()
=![]()
QED
Proposition 3.2.
Given the disjoint primary set K and the violational transformation Tp defined in [D3.4], then the number of elements in Tp(K) differs from the number of elements in K by m, or:
![]()
Proof:
Let
K contain a information-hidden elements and![]() violational
elements. Thus, by definition:
violational
elements. Thus, by definition:
![]() (i)
(i)
Let K*=Tp(K,m). By definition Tp leaves the number of information-hidden elements unchanged, therefore:
![]() (ii)
(ii)
Also by definition of Th:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]() (iv)
(iv)
Substituting (i) into (iv) gives:
![]()
QED
Proposition 3.3.
Given the encapsulated set G with an ith disjoint primary set Ki and given that a particular xth disjoint primary set Kx only is subject to the violational transformation Tp defined in [D3.4], the number of violational elements in Tp(G) is given by:
![]()
Proof:
By proposition 1.3.6 in [1]:
![]()
=![]() (i)
(i)
Let G*=Tp(x,G,m) and let Ki*=Tp(Ki,m). By definition:
![]()
=![]() (ii)
(ii)
By the definition of Th:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]() (iv)
(iv)
Also by the definition of Th:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]() (vi)
(vi)
Substituting (i) into (vi) gives:
![]()
QED
Proposition 3.4.
Given the disjoint primary set K and the hidden element transformation Tz defined in [D3.5], then the number of elements in Tz(K) differs from the number of elements in K by m, or:
![]()
Proof:
Let
K contain a information-hidden elements and![]() violational
elements. Thus, by definition:
violational
elements. Thus, by definition:
![]() (i)
(i)
Let K*=Tz(K,m). By definition Tz leaves the number of violational elements unchanged, therefore:
![]() (ii)
(ii)
Also by definition of Tz:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]() (iv)
(iv)
Substituting (i) into (iv) gives:
![]()
QED
Proposition 3.5.
Given the encapsulated set G with an ith disjoint primary set Ki and given that a particular xth disjoint primary set Kx only is subject to the hidden element transformation Tz defined in [D3.5], the number of violational elements in Tz(G) is given by:
![]()
Proof:
Let G*=Tz(x,G,m) and let Ki*=Tz(Ki,m). By definition:
![]() (i)
(i)
By the definition of Tz:
![]() (ii)
(ii)
Substituting (ii) into (i) gives:
![]()
QED
Proposition 3.6.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and internal potential coupling sin(Qi),
the change of internal potential coupling
elements
and internal potential coupling sin(Qi),
the change of internal potential coupling![]() when
the number of violational elements in Ki
changes by m where
when
the number of violational elements in Ki
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tp be the violational transformation defined in [D3.4] and let Ki*=Tp(Ki,m). By definition [D3.1], the change of internal potential coupling effected by applying Tp to Qi is:
![]() (i)
(i)
By proposition 1.2:
![]() (ii)
(ii)
By proposition 3.2:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]()
=![]()
=![]() (iv)
(iv)
But:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]()
![]()
And therefore by (i):
![]()
QED
Proposition 3.7.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of internal potential coupling sin(Qi),
the change of internal potential coupling of the entire
set![]() when
the number of violational elements
in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of violational elements
in a particular
xth
disjoint primary set Kx
changes by m where![]() is
equal to the change of internal potential coupling of Kx,
or:
is
equal to the change of internal potential coupling of Kx,
or:
![]()
Proof:
By proposition 1.3.11 of [1], the internal potential coupling of G is the sum of the internal potential coupling of all its disjoint primary sets:
![]()
=![]() (i)
(i)
Let Tp be the violational transformation defined in [D3.4] and let Ki*=Tp(Ki,m). Furthermore, let Tp apply to the xth disjoint primary set only such that Kx*=Tp(Kx,m) and G*=Tp(x,G,m). By definition:
![]()
=![]() (ii)
(ii)
By definition [D3.3], the change of internal potential coupling of G effected by applying transformation Tp to G is given by:
![]() (iii)
(iii)
Substituting (i) and (ii) into (iii) gives:
![]() (iv)
(iv)
But as Tp is only applied to Kx then all disjoint primary sets except Kx are unchanged, or:
![]()
And therefore:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]()
=![]() (vi)
(vi)
By definition [D3.1], the change of internal potential coupling effected by applying Tp to Kx is then:
![]() (vii)
(vii)
Substituting (vii) into (vi) gives:
![]()
QED
Proposition 3.8.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and external potential coupling
elements
and external potential coupling![]() ,
the change of external potential coupling
,
the change of external potential coupling![]() when
the number of violational elements in Ki
changes by m where
when
the number of violational elements in Ki
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tp be the violational transformation defined in [D3.4]; let Ki*=Tp(Ki,m) and let G*=Tp(G,m).
By definition [D3.2], the change of external potential coupling effected by applying Tp to Ki is then:
![]() (i)
(i)
By proposition 1.4 in [1]:
![]() (ii)
(ii)
By proposition 3.3:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]() (iv)
(iv)
By proposition 3.2:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]()
=![]()
=![]()
=![]()
=![]() (vi)
(vi)
But:
![]() (vii)
(vii)
Substituting (vii) into (vi) gives:
![]()
![]()
And therefore by (i):
![]()
QED
Proposition 3.9.
Given the encapsulated set G
of n elements with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and external potential coupling
elements
and external potential coupling![]() ,
the change of external potential coupling of the entire
set
,
the change of external potential coupling of the entire
set![]() when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
By proposition 1.3.12 of [1], the external potential coupling of G is the sum of the external potential coupling of all its disjoint primary sets:
![]()
=![]() (i)
(i)
Let Tp be the violational transformation defined in [D3.4] and let Ki*=Tp(Ki,m). Furthermore, let Tp apply to the xth disjoint primary set only such that Kx*=Tp(Kx,m) and G*=Tp(x,G,m). By definition:
![]()
=![]() (ii)
(ii)
By definition [D3.2]:
![]() (iii)
(iii)
Substituting (i) and (ii) into (iii) gives:
![]() (iv)
(iv)
By definition [D3.2]:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]() (vi)
(vi)
By proposition 1.4 in [1]:
![]() (vii)
(vii)
If
we consider Ki
where![]() then
as Tp
is applied only to Kx
then:
then
as Tp
is applied only to Kx
then:
![]() (viii)
(viii)
Substituting (viii) into (vii) gives:
![]() (ix)
(ix)
By proposition 3.3:
![]() (x)
(x)
Substituting (x) into (ix) gives:
![]()
=![]()
=![]() (xi)
(xi)
But:
![]() (xii)
(xii)
Substituting (xi) into (xii) gives:
![]()
As
this holds![]() we
can take the sum over all primary sets except x:
we
can take the sum over all primary sets except x:
![]()
=![]() (xiii)
(xiii)
By definition,
![]()
So:
![]() (xiv)
(xiv)
Substituting (xiv) into (viii) gives:
![]()
![]() (xv)
(xv)
Substituting (xv) into (vi) gives:
![]()
=![]()
QED
Proposition 3.10.
Given the encapsulated set G
of n elements with an ith
disjoint primary set Ki
of![]() elements
and external potential coupling sex(Ki),
the change of external potential coupling of the entire
set
elements
and external potential coupling sex(Ki),
the change of external potential coupling of the entire
set![]() when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tp be the violational transformation defined in [D3.4] and let it apply to the xth disjoint primary set only. By proposition 3.8, the change of external potential coupling of Kx by the application of Tp to Kx is given by:
![]() (i)
(i)
By proposition 3.9, the change of external potential coupling of the entire set G by the application of Tp to Kx is given by:
![]() (ii)
(ii)
Substituting (ii) into (i) gives:
![]()
QED
Proposition 3.11.
Given the encapsulated set G
of n elements with an ith
disjoint primary set Ki
of![]() elements,
the change of potential coupling of the entire set
elements,
the change of potential coupling of the entire set![]() when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of violational elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tp be the violational transformation defined in [D3.4] and let Ki*=Tp(Ki,m). Furthermore, let Tp apply to the xth disjoint primary set only such that Kx*=Tp(Kx,m) and G*=Tp(x,G,m). From proposition 3.7, when the number of violational elements in Kx changes by m, the change of internal potential coupling of the entire set is given by:
![]() (i)
(i)
By proposition 3.6, when the number of violational elements in Kx changes by m, the change of internal potential coupling of Kx is given by
![]() (ii)
(ii)
Substituting (ii) into (i) gives:
![]() (iii)
(iii)
From proposition 3.10, when the number of violational elements in Kx changes by m, the change of external potential coupling is given by:
![]() (iv)
(iv)
By proposition 3.1, the change of potential coupling of G is given by:
![]() (v)
(v)
Substituting (iii) and (iv) into (v) gives:
![]()
=![]()
QED
Proposition 3.12.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and internal potential coupling sin(Ki),
the change of internal potential coupling
elements
and internal potential coupling sin(Ki),
the change of internal potential coupling![]() when
the number of information-hidden elements in Ki
changes by m where
when
the number of information-hidden elements in Ki
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tz be the hidden transformation defined in [D3.5] and let Ki*=Tz(Ki,m). By definition [D3.1], the change of internal potential coupling effected by applying Tz to Ki is:
![]() (i)
(i)
By proposition 1.2 in [1]:
![]() (ii)
(ii)
By proposition 3.4:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]()
=![]()
=![]() (iv)
(iv)
But:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]()
![]()
And therefore by (i):
![]()
QED
Proposition 3.13.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of internal potential coupling![]() ,
the change of internal potential coupling of the entire
set
,
the change of internal potential coupling of the entire
set![]() when
the number of information-hidden elements
in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of information-hidden elements
in a particular
xth
disjoint primary set Kx
changes by m where![]() is
equal to the change of internal potential coupling of Kx,
or:
is
equal to the change of internal potential coupling of Kx,
or:
![]()
Proof:
By proposition 1.3.11 in [1], the internal potential coupling of G is the sum of the internal potential coupling of all its disjoint primary sets:
![]()
=![]() (i)
(i)
Let Tz be the hidden transformation defined in [D3.5] and let Ki*=Tp(Ki,m). Furthermore, let Tz apply to the xth disjoint primary set only such that Kx*=Tp(Kx,m) and G*=Tz(x,G,m). By definition:
![]()
=![]() (ii)
(ii)
By definition [D3.1], the change of internal potential coupling of G effected by applying transformation Tz to G is:
![]() (iii)
(iii)
Substituting (i) and (ii) into (iii) gives:
![]() (iv)
(iv)
But as Tz is only applied to Kx then all disjoint primary sets except Kx are unchanged, or:
![]()
And therefore:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]()
=![]() (vi)
(vi)
By definition [D3.1], the change of internal potential coupling effected by applying Tz to Kx is then:
![]() (vii)
(vii)
Substituting (vii) into (vi) gives:
![]()
QED
Proposition 3.14.
Given the encapsulated set G
with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and external potential coupling
elements
and external potential coupling![]() ,
the change of external potential coupling
,
the change of external potential coupling![]() when
the number of information-hidden elements in Ki
changes by m where
when
the number of information-hidden elements in Ki
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tz be the hidden transformation defined in [D3.5]; let Ki*=Tz(Ki,m) and let G*=Tz(G,m).
By definition [D3.2], the change of external potential coupling effected by applying Tz to Ki is then:
![]() (i)
(i)
By proposition 1.4 in [1]:
![]() (ii)
(ii)
By proposition 3.5:
![]() (iii)
(iii)
Substituting (iii) into (ii) gives:
![]() (iv)
(iv)
By definition of Tz:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]() (vi)
(vi)
By proposition 3.4:
![]() (vii)
(vii)
Substituting (vii) into (vi) gives:
![]()
=![]()
=![]() (viii)
(viii)
But:
![]() (ix)
(ix)
Substituting (ix) into (viii) gives:
![]()
![]()
And therefore by (i):
![]()
QED
Proposition 3.15.
Given the encapsulated set G
of n elements with an
ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and external potential coupling
elements
and external potential coupling![]() ,
the change of external potential coupling of the entire
set
,
the change of external potential coupling of the entire
set![]() when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
By proposition 1.3.12 in [1], the external potential coupling of G is the sum of the external potential coupling of all its disjoint primary sets:
![]()
=![]() (i)
(i)
Let Tz be the hidden transformation defined in [D3.5] and let Ki*=Tz(Ki,m). Furthermore, let Tz apply to the xth disjoint primary set only such that Kx*=Tz(Kx,m) and G*=Tz(x,G,m). By definition:
![]()
=![]() (ii)
(ii)
By definition [D3.2]:
![]() (iii)
(iii)
Substituting (i) and (ii) into (iii) gives:
![]() (iv)
(iv)
By definition [D3.2]:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]() (vi)
(vi)
By proposition 1.4:
![]() (vii)
(vii)
If
we consider Ki
where![]() then
as Tz
is applied only to Kx
then:
then
as Tz
is applied only to Kx
then:
![]() (viii)
(viii)
Substituting (viii) into (vii) gives:
![]() (ix)
(ix)
By proposition 3.5:
![]() (x)
(x)
Substituting (x) into (ix) gives:
![]() (xi)
(xi)
But by proposition 1.4 in [1]:
![]() (xii)
(xii)
Substituting (xii) into (xi) gives:
![]()
As
this holds![]() we
can take the sum over all primary sets except x:
we
can take the sum over all primary sets except x:
![]() (xiii)
(xiii)
Substituting (xiii) into (vi) gives:
![]()
QED
Proposition 3.16.
Given the encapsulated set G
of n elements with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements
and external potential coupling
elements
and external potential coupling![]() ,
the change of external potential coupling of the entire
set
,
the change of external potential coupling of the entire
set![]() when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tz be the hidden transformation defined in [D3.5] and let Ki*=Tz(Ki,m). Furthermore, let Tz apply to the xth disjoint primary set only such that Kx*=Tz(Kx,m) and G*=Tz(x,G,m). By proposition 3.14, the change of external potential coupling of Kx by the application of Tz to Kx is given by:
![]() (i)
(i)
By proposition 3.15, the change of external potential coupling of the entire set G by the application of Tz to Kx is the same as the change of external potential coupling of Kx or:
![]() (ii)
(ii)
Substituting (i) into (ii) gives:
![]()
QED
Proposition 3.17.
Given the encapsulated set G
of n elements with an ith
primary set Qi and an
ith
disjoint primary set Ki
of![]() elements,
the change of potential coupling of the entire set
elements,
the change of potential coupling of the entire set![]() when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where
when
the number of information-hidden elements in a particular
xth
disjoint primary set Kx
changes by m where![]() is
given by:
is
given by:
![]()
Proof:
Let Tz be the hidden transformation defined in [D3.5] and let Ki*=Tz(Ki,m). Furthermore, let Tz apply to the xth disjoint primary set only such that Kx*=Tz(Kx,m) and G*=Tz(x,G,m). From proposition 3.13, when the number of information-hidden elements in Kx changes by m, the change of internal potential coupling of the entire set is given by:
![]() (i)
(i)
By proposition 3.12, when the number of information-hidden elements in Kx changes by m, the change of internal potential coupling of Kx is given by
![]() (ii)
(ii)
Substituting (ii) into (i) gives:
![]() (iii)
(iii)
From proposition 3.16, when the number of information-hidden elements in Kx changes by m, the change of external potential coupling is given by:
![]() (iv)
(iv)
By proposition 3.1, the change of potential coupling of G is given by:
![]() (v)
(v)
Substituting (iii) and (iv) into (v) gives:
![]()
QED
Proposition 3.18.
Given
the encapsulated set G of n elements,
the cumulative change of potential coupling of the entire
set![]() when
m violational elements are moved from a particular
source disjoint primary set Ks
to a different target disjoint
primary set Kt
is given by:
when
m violational elements are moved from a particular
source disjoint primary set Ks
to a different target disjoint
primary set Kt
is given by:
![]()
Proof:
Let Tp1 be the violational transformation defined in [D3.4] and let Tp1 apply to the sth disjoint primary set Ks only such that Ks*=Tp1(Ks,m) and G*=Tp1(s,G,m). Tp1 will remove m violational elements from Ks.
Let
Tp2 be the violational transformation
defined in [D3.4] and let Tp2 apply
to the tth
disjoint primary set Kt
where![]() only
such that Kt*=Tp2(Kt,m)
and G**=Tp2(t,G*,m).
Tp2 will add m violational elements from
Kt.
only
such that Kt*=Tp2(Kt,m)
and G**=Tp2(t,G*,m).
Tp2 will add m violational elements from
Kt.
Let us define the violational translation transformation TTp as the combination of the two translations Tp1 and Tp2 such that:
TTp (G)= Tp2(Tp1 (G))
As these transformations are linear, the change of the potential coupling of TTh is equal to the sum of the changes of the potential coupling of the transformations Tp2 and Tp1, or:
![]() (i)
(i)
Considering elements removed from a disjoint primary set as negative, then Tp1 will add -m elements to G. By proposition 3.11, the change of potential coupling in G caused by the removal of these m violational elements from Ks is given by:
![]() (ii)
(ii)
Substituting -m for m in (ii) gives:
![]() (iii)
(iii)
By proposition 3.11 again, the change of potential coupling in G* caused by the addition of m violational elements to Kt is given by:
![]() (iv)
(iv)
G* has m fewer elements than G and they are all information-hiding violational, and thus both v(G*) and n* are changed in comparison with G, such that:
![]() (v)
(v)
![]() (vi)
(vi)
Substituting (v) and (vi) into (iv) gives:
![]()
=![]()
=![]() (vii)
(vii)
Substituting (iii) and (vii) into (i) gives:
![]()
=![]() (viii)
(viii)
By definition [D3.6]:
![]()
![]() (ix)
(ix)
Substituting (ix) into (viii) gives:
![]()
QED
Proposition 3.19.
Given
the encapsulated set G, the cumulative change of potential coupling
of the entire set![]() when
m information-hidden elements are moved from a particular
source disjoint primary set Ks
to a different target disjoint
primary set Kt
is given by:
when
m information-hidden elements are moved from a particular
source disjoint primary set Ks
to a different target disjoint
primary set Kt
is given by:
![]()
Proof:
Let Tz1 be the hidden transformation defined in [D3.5] and let Tz1 apply to the sth disjoint primary set Ks only such that Ks*=Tz1(Ks,m) and G*=Tz1(s,G,m). Tz1 will remove m information-hidden elements from Ks.
Let
Tz2 be the hidden transformation defined in
[D3.5] and let Tz2 apply to the
tth![]() disjoint
primary set Kt only such that Kt*=Tz2(Kt,m)
and G**=Tz2(t,G*,m).
Tz2 will add m information-hidden
elements from Kt.
disjoint
primary set Kt only such that Kt*=Tz2(Kt,m)
and G**=Tz2(t,G*,m).
Tz2 will add m information-hidden
elements from Kt.
Let us define the hidden translation transformation TT as the combination of the two translations Tz1 and Tz2 such that:
TT (G)= Tz2(Tz1 (G))
As these transformations are linear, the change of the potential coupling of TT is equal to the sum of the changes of the potential coupling of the transformations Tz2 and Tz1, or:
![]() (i)
(i)
Considering elements removed from a disjoint primary set as negative, then Tz1 will add -m elements to G. By proposition 3.17, the change of potential coupling in G caused by the removal of these m information-hidden elements from Ks is given by:
![]() (ii)
(ii)
Substituting -m for m in (ii) gives:
![]() (iii)
(iii)
By proposition 3.17 again, the change of potential coupling in G* caused by the addition of m information-hidden elements to Kt is given by:
![]() (iv)
(iv)
G* has m fewer elements than G but they are all information-hidden, and thus v(G*) is unchanged, or:
![]() (v)
(v)
Substituting (v) into (iv) gives:
![]() (vi)
(vi)
Substituting (iii) and (vi) into (i) gives:
![]()
=![]()
QED
Proposition 3.20.
Given
the encapsulated set G of n elements,
the cumulative change of potential coupling of the entire
set![]() when
m information-hidden elements in a particular
disjoint primary set Kx
are converted to violational elements within the same
disjoint primary set is given by:
when
m information-hidden elements in a particular
disjoint primary set Kx
are converted to violational elements within the same
disjoint primary set is given by:
![]()
Proof:
Let Tz be the hidden transformation defined in [D3.5] and let Tz apply to the xth disjoint primary set Kx only such that Kx*=Tz(Kx,m) and G*=Tz(x,G,m). Tz will remove m information-hidden elements from Kx.
Let Tp be the violational transformation defined in [D3.4] and let Tp apply to the xth disjoint primary set Kx only such that Kx*=Tp(Kt,m) and G**=Tp(x,G*,m). Tp will add m violational elements from Kx.
Let us define the conversion transformation TC as the combination of the two translations Tz and Tp such that:
TC (G)= Tp(Tz (G))
As these transformations are linear, the change of the potential coupling of TC is equal to the sum of the changes of the potential coupling of the transformations Tp and Tz, or:
![]() (i)
(i)
Considering elements removed from a disjoint primary set as negative, then Tz will add -m elements to G. By proposition 3.17, the change of potential coupling in G caused by the removal of these m information-hidden elements from Kx is given by:
![]() (ii)
(ii)
Substituting -m for m in (ii) gives:
![]() (iii)
(iii)
By proposition 3.11, the change of potential coupling in G* caused by the addition of m violational elements to Kx is given by:
![]() (iv)
(iv)
Kx* has m fewer elements than K and they are all information-hidden, and thus both Kx* and n* are changed in comparison with G, but v(Kx*) and v(G*) are unchanged such that:
![]() (v)
(v)
![]() (vi)
(vi)
![]() (vii)
(vii)
![]() (viii)
(viii)
Substituting (v), (vi), (vii) and (viii) into (iv) gives:
![]()
=![]()
=![]() (ix)
(ix)
Substituting (iii) and (ix) into (i) gives:
![]()
=
![]()
QED
8. References
[1] "Encapsulation theory fundamentals," Ed Kirwan, www.EdmundKirwan.com/pub/paper1.pdf
[2] "Encapsulation theory: the transformation equations of absolute information hiding," Ed Kirwan, www.EdmundKirwan.com/pub/paper3.pdf
*© Edmund Kirwan 2009-2010. Revision 1.11 January 5th 2010. (Original revision 1.0 written January 12th 2009.) arXiv.org is granted a non-exclusive and irrevocable licence to distribute this article; all other entities may republish, but not for profit, all or part of this material provided reference is made to the author and the title of this paper. The latest version of this paper is available at [2].
1This justifies the notion of the interface repository in computer programming, a subsystem holding only public interfaces that act as facades to various other subsystems of hidden implementations.