Encapsulation theory: a format for exercises.
Edmund Kirwan*
Abstract
This paper presents a format in which simple problems and exercises of encapsulation theory can be framed to facilitate the calculating of potential coupling for simple encapsulated sets.
Keywords
Encapsulation theory, encapsulation, potential coupling, exercises.
1. Introduction
This paper proposes no new terms, definitions or equations.
This paper, in fact, proposes nothing new of any significance whatsoever.
Instead, this paper proposes a loose format in which potential coupling [2] problems may be presented and solved. There are two reasons for this.
Firstly, encapsulation theory was developed primarily as an analytical tool to aid in the design of computer programs, yet the connection between the theory's equations and the programs themselves is often obscure. The format tries to capture, in a simplified if slightly abstract sense, this connection in an attempt to show the relevance of the equations at least to small programs. (Calculating the potential coupling of large programs is, however, a task for machines.)
Secondly, the next paper [4] in this series to be written requires some rather subtle manipulation to the distribution of elements within disjoint primary sets, and these manipulations are best demonstrated through example. A means of providing a consistent framework in which such examples could be presented was considered, therefore, a prerequisite.
This paper considers encapsulated sets of absolute information-hiding only.
2. Format
To begin with an example, we consider an encapsulated set G consisting of a single disjoint primary set K1 (the associated primary set Q1 is understood) in which reside five violational elements and three information-hidden elements. This may be graphically shown as in figure 1, where the information-hiding violational elements are coloured black and the information-hidden elements are coloured white.
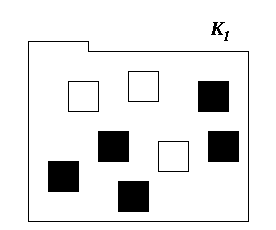
Figure 1: A disjoint primary set with 8 elements, 5 violational and 3 information-hidden.
Let us, purely for convenience, re-arrange the contained elements of figure 1 so that the violational elements are, "On top," of the information-hidden elements, see figure 2.
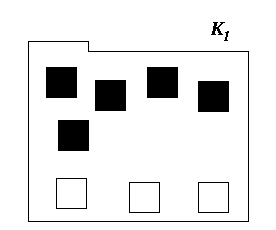
Figure 2: A disjoint primary set with 8 elements, 5 violational on top and 3 information-hidden on the bottom.
To make figure 2 more descriptive, let us clearly state three more parameters of G that will be useful in the upcoming calculations, namely the number of elements n, the number of disjoint primary sets r and the specific violational density of the set, d (recall that the specific violation density is the number of violational elements in the set divided by the number of disjoint primary sets). See figure 3.
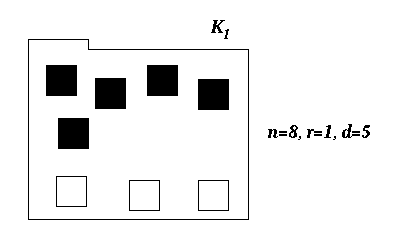
Figure 3: A disjoint primary set with 8 elements, 5 violational and 3 information-hidden, with key parameters listed.
Now let us take an abstraction of figure 3, showing the disjoint primary set as merely two vertical lines whose name, K1, appears outside the lines, to the upper right. Within the lines, instead of showing a graphical representation of the elements, we shall show only the numbers of elements contained in the disjoint primary set; the number of violational elements shall be shown, "On top," above the number of information-hidden elements, see (A.i).
![]() n=8,
r=1, d=5 (A.i)
n=8,
r=1, d=5 (A.i)
In (A.i) we thus have the number 5 - the number of violational elements in the disjoint primary set - above the number 3 - the number of information-hidden elements in the disjoint primary set. We see that the name of the set, G, does not appear in the format and is simply understood.
Let us take a second example, see (A.ii).
![]() n=23,
r=2,
n=23,
r=2,![]() (A.ii)
(A.ii)
Example (A.ii) shows us a set of two disjoint primary sets, K1 and K2. K1 has 10 violational elements and 7 hidden elements. K2 has 1 violational element and 5 hidden elements. Outside the regions, we see the number of elements n is 23, the number of regions r is 2 and the specific violational density of the set d is 5.5.
Let us take a third example, see (A.iii).
![]() n=79,
r=3,
n=79,
r=3,![]() (A.iii)
(A.iii)
Example (A.iii)
shows us a set of three disjoint primary sets, K1,
K2 and K3. K1
has 60 violational elements and 17 hidden elements. K2
and K3 have 1 violational element and
0 hidden elements each. Outside the regions, we see the number
of elements n is 79, the number of regions r is
3 and the specific violational density of the set d
is![]() .
.
Recall that from [2] that the
number of violational elements of a disjoint primary set K is
the cardinality of the information-hiding violation function,![]() ,
and from [3] that the number of information-hidden elements is the
cardinality of the information-hiding function,
,
and from [3] that the number of information-hidden elements is the
cardinality of the information-hiding function,![]() .
Thus the general form of the format as given so far for a set of r
disjoint primary sets is:
.
Thus the general form of the format as given so far for a set of r
disjoint primary sets is:
![]()
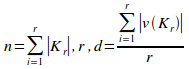
The format is not complete, however, until we have established the connection between the sets represented and their potential coupling. We shall proceed with task in the next section.
3. Calculating the potential coupling
Let us again consider an example already presented, see (B.i).
![]() n=23,
r=2,
n=23,
r=2,![]() (B.i)
(B.i)
What is the potential coupling of this encapsulated set?
Again from [2] we know that the potential coupling of an encapsulated set is the sum of the potential couplings of all its primary sets. So the question becomes: what is the potential coupling of the sets displayed here?
Let us consider the first disjoint primary set, K1. This has an associated primary set, Q1, but this is not shown as the potential coupling is primarily a function of disjoint primary sets. The potential coupling of a primary set is defined as the sum of its internal potential coupling and its external potential coupling.
The internal potential coupling of a primary set is the total number of elements in its disjoint primary set multiplied by the total number of elements minus one in that disjoint primary set (see [2], proposition 1.2). The total number of elements in K1 is 17. Thus the internal potential coupling of K1 is 17 x 16.
The external potential coupling of a primary set is the number of elements in its disjoint primary set multiplied by the number of violational elements in all other disjoint primary sets (see [2], proposition 1.4). Thus the external potential coupling of Q1 (associated with K1) is 17 x 1.
The potential coupling of Q1,
written![]() ,
is then the sum of these two terms:
,
is then the sum of these two terms:![]() =
17 x 16 + 17 x 1.
=
17 x 16 + 17 x 1.
We
can simplify this equation to read:![]() =
17(16 + 1). This is the key form of the equation, which will be
presented under the sets in our format: the potential coupling of a
primary set is the number of elements in its disjoint primary
multiplied by the number of elements minus one in that disjoint
primary set plus the sum of the violational elements in all other
disjoint primary sets.
=
17(16 + 1). This is the key form of the equation, which will be
presented under the sets in our format: the potential coupling of a
primary set is the number of elements in its disjoint primary
multiplied by the number of elements minus one in that disjoint
primary set plus the sum of the violational elements in all other
disjoint primary sets.
We shall add this equation to (B.i) and re-write it as:
![]() n=23,
r=2,
n=23,
r=2,![]() (B.ii)
(B.ii)
![]() =
17(16 + 1) = 289
=
17(16 + 1) = 289
Now let us apply the same equation to K2. The potential coupling of K2 is the number of elements in K2 (6) multiplied by the number of elements minus one in K2 (5) plus the sum of the violational elements in all other disjoint primary sets (10).
This gives us: s(K2) = 6(5 + 10). Let us add this to our format, also, see (B.iii).
![]() n=23,
r=2,
n=23,
r=2,![]() (B.iii)
(B.iii)
![]() =
17(16 + 1) = 289
=
17(16 + 1) = 289
![]() =
6(5 + 10) = 90
=
6(5 + 10) = 90
The potential coupling of the
encapsulated set is then just the sum of these terms:![]() =
289 + 90. Adding this to our set gives the next evolution of the
format, see (B.iv).
=
289 + 90. Adding this to our set gives the next evolution of the
format, see (B.iv).
![]() n=23,
r=2,
n=23,
r=2,![]() (B.iv)
(B.iv)
![]() =
17(16 + 1) = 289
=
17(16 + 1) = 289
![]() =
6(5 + 10) = 90
=
6(5 + 10) = 90
![]() =
289 + 90 = 379
=
289 + 90 = 379
As a slight aside, if we consider for a moment that the set in (B.iv) is a Java system of two packages with 10 public classes and 7 package-private classes in one package and 1 public class and 5 package-private classes in the other, then the maximum possible number of source code dependencies between these 23 classes in this configuration would be 379.
For comparison, let us also take our other system in (A.iii) and re-write it here using the latest format, see (B.v).
![]() n=79,
r=3,
n=79,
r=3,![]() (B.v)
(B.v)
![]() =77(76
+ 1 + 1) = 6006
=77(76
+ 1 + 1) = 6006
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =
6128
=
6128
The format is still not complete, however, because it only presents the potential coupling of the system. We need finally to add the equations for the uniform potential coupling and the minimum isoledensal potential coupling; in this way, the three key equations of encapsulation theory and the sample sets they describe can be gathered together for examination.
4. The uniform potential coupling
Most encapsulated sets are not uniformly distributed in violational and information-hidden elements, but it is often interesting to calculate what would the potential coupling of an encapsulated set be if it were so distributed. The equation for this uniform potential coupling su(G) is given by (see [2], proposition 1.8):
![]()
In our format developed so far, we clearly list the three variables n, r and d beside the set being described, thus it is a simple matter to add this equation to our format to give us - if we take (B.iv) as an example - the following:
![]() n=23,
r=2,
n=23,
r=2,![]() (C.i)
(C.i)
![]() =
17(16 + 1) = 289
=
17(16 + 1) = 289
![]() =
6(5 + 10) = 90
=
6(5 + 10) = 90
![]() =
289 + 90 = 379
=
289 + 90 = 379
![]()
Of course, we note that if we uniformly distribute the information-hidden and violational elements of this encapsulated set then we will arrive at a set not with whole numbers but with rationals:
![]()
No Java system, for example, can have 5.5 public classes in a package; this reflects the statistical nature of the uniform potential coupling equation and reminds us, while that perfectly uniform distribution may not in all cases be possible, the larger the set under observation, the closer the approximation of uniform distribution is achievable.
To add our uniform potential coupling equation to our other example (B.v), we arrive at (C.ii).
![]() n=79,
r=3,
n=79,
r=3,![]() (C.ii)
(C.ii)
![]() =77(76
+ 1 + 1) = 6006
=77(76
+ 1 + 1) = 6006
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =
6128
=
6128
![]()
5. The isoledensal potential coupling
As described in [2], the isoledensal transformation maps a set to the set with the lowest uniform potential coupling conserving the total number of elements and the violation density of the original encapsulated set. The equation for this isoledensal potential coupling sild(G) is given by (see [2], proposition 1.14):
![]()
Again, these variables are readily available, and with the presentation of this equation we come to the final form of our format. If we take (C.i) above, then its final form is:
![]() n=23,
r=2,
n=23,
r=2,![]() (D.i)
(D.i)
![]() =
17(16 + 1) = 289
=
17(16 + 1) = 289
![]() =
6(5 + 10) = 90
=
6(5 + 10) = 90
![]() =
289 + 90 = 379
=
289 + 90 = 379
![]()
![]()
And if we take (C.ii) from above we have:
![]() n=79,
r=3,
n=79,
r=3,![]() (D.ii)
(D.ii)
![]() =77(76
+ 1 + 1) = 6006
=77(76
+ 1 + 1) = 6006
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =1(0
+ 61) = 61
=1(0
+ 61) = 61
![]() =
6128
=
6128
![]()
![]()
6. Transformation examples
In [3] equations were derived which described how the potential coupling of a set changes as elements are added, removed and moved between disjoint primary sets. We shall examine some sample sets to confirm that these equations indeed give the correct results.
First, consider the set of three disjoint primary sets as shown:
![]() n=61,
r=3,
n=61,
r=3,![]() (D.i)
(D.i)
![]() =
20(19 + 7 + 9) = 700
=
20(19 + 7 + 9) = 700
![]() =
12(11 + 3 + 9) = 276
=
12(11 + 3 + 9) = 276
![]() =
29(28 + 3 + 7) = 1102
=
29(28 + 3 + 7) = 1102
![]() =
700 + 276 + 1102 = 2078
=
700 + 276 + 1102 = 2078
![]()
![]()
Now, let us add 5 violational elements to K1. The equation which describes how the potential coupling of our set will change due to these added elements is given by the first transformation equation (see [3], proposition 3.11):
![]()
If we take m=5 and x=1 such that Kx=K1, then this equation predicts that the potential coupling of (D.i) will change by the following amount:
![]()
If we now actually perform the transformation and add the 5 violational elements to set (D.i), then we get:
![]() n=66,
r=3,
n=66,
r=3,![]() (D.ii)
(D.ii)
![]() =
25(24 + 7 + 9) = 1000
=
25(24 + 7 + 9) = 1000
![]() =
12(11 + 8 + 9) = 336
=
12(11 + 8 + 9) = 336
![]() =
29(28 + 8 + 7) = 1247
=
29(28 + 8 + 7) = 1247
![]() =
1000 + 336 + 1247 = 2583
=
1000 + 336 + 1247 = 2583
![]()
![]()
And as we can see, if take the s(G) in (D.i) from that in (D.ii) we get: 2583 - 2078 = 505, as expected.
If we now keep our set (D.ii), let's perform a second transformation on it: consider moving 10 information-hidden elements from K3 to K2. The equation which describes how the potential coupling of our set will change due to these translated elements is given by the fourth transformation equation (see [3], proposition 3.19):
![]()
As we are moving elements from K3 to K2 then the source disjoint primary set Ks=K3, and the target disjoint primary set Kt=K2 . With m=10, we then have:
![]()
If we now actually perform the transformation and move the 10 information-hidden elements from K3 to K2, then we get:
![]() n=66,
r=3,
n=66,
r=3,![]() (D.iii)
(D.iii)
![]() =
25(24 + 7 + 9) = 1000
=
25(24 + 7 + 9) = 1000
![]() =
22(21 + 8 + 9) = 836
=
22(21 + 8 + 9) = 836
![]() =
19(18 + 8 + 7) = 627
=
19(18 + 8 + 7) = 627
![]() =
1000 +836 + 627 = 2463
=
1000 +836 + 627 = 2463
![]()
![]()
And as we can see, if take
the![]() in
(D.ii) from that in (D.iii) we get: 2463 - 2583 = -120, as
expected.
in
(D.ii) from that in (D.iii) we get: 2463 - 2583 = -120, as
expected.
7. Conclusions
There are no real conclusions to this paper as the paper proposed no new arguments and instead only presented a loose format in which sample problems of encapsulation theory can be worked out in the hope of clarifying the equations employed for interested students.
8. Related work
-
9. References
[1] "Encapsulation theory: a format for exercises," Ed Kirwan, www.EdmundKirwan.com/pub/paper4.pdf
[2] "Encapsulation theory fundamentals," Ed Kirwan, www.EdmundKirwan.com/pub/paper1.pdf
[3] "Encapsulation theory: the transformation equations of absolute information-hiding," Ed Kirwan, www.EdmundKirwan.com/pub/paper3.pdf
[4] "Encapsulation theory: the anomalous minimised configuration," Ed Kirwan, www.EdmundKirwan.com/pub/paper5.pdf
*© Edmund Kirwan 2009. Revision 1.4 January 5th 2010. (Revision 1.0: 2008.) arXiv.org is granted a non-exclusive and irrevocable licence to distribute this article; all other entities may republish, but not for profit, all or part of this material provided reference is made to the author and the title of this paper. The latest version of this paper is available at [1].