
Structure and the FBI.
A hypothetical question.
Let's say you're an FBI agent.
One day, you find yourself at the Lincoln Center in Manhattan, New York, and desperately need to get to the Rockefeller Center on foot. You happen to know, however, that you are being followed by a foreign spy. Let's say his name is, oh, Dmitri Evgenii Gurkovsky ("The Australian"). What path do you take? Examine figure 1 for a moment to make your decision; Lincoln Center lies at the top and the Rockefeller Center at the bottom.
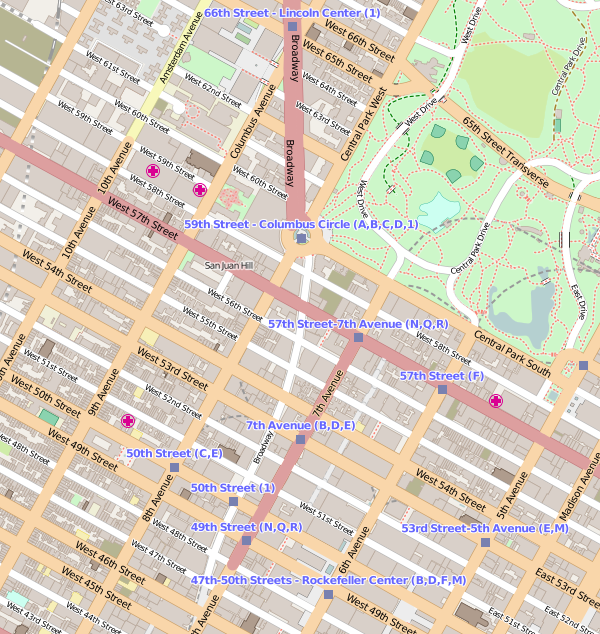
Figure 1: Your path awaits you.
Figure 2 shows one possibility.
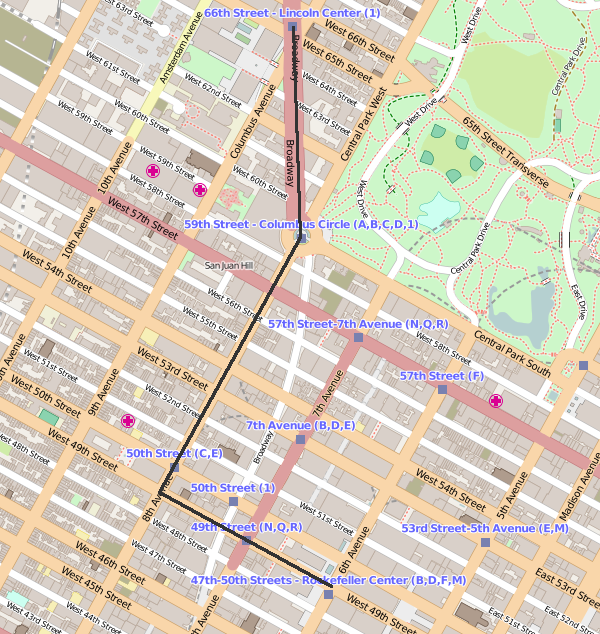
Figure 2: Wrong!
If your chosen path resembles that shown in figure 2 then Dmitri will probably have you strapped to a chair before nightfall, serving you delicious fruity cocktails of benzodiazepine and sodium thiopental. You have chosen the wrong path (both in actuality and career).
For once, counter-intelligence trade-craft seems to match its depiction in the movies. The police, self-defence instructors, security specialists, news reporters, vacationing celebrities: all will tell you, if you want to, "Shake a tail," do not take the direct or obvious path to your destination. Always leave your stalker guessing. Take an elaborate, circuitous route.
Hence figure 3 shows a better choice.
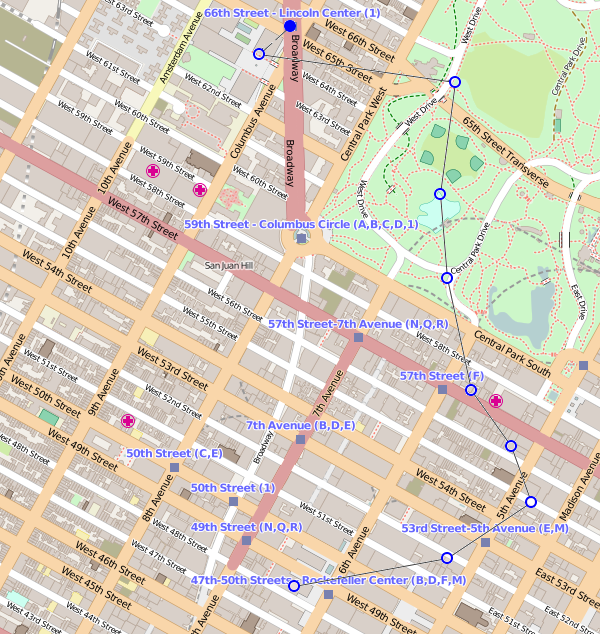
Figure 3: A better way to the Rock.
In figure 3, you exit Lincoln Centre and make straight for the department store across the road. Then you head into Central Park. Of course you do: everyone evades stalkers in Central Park; it's practically what Central Park is for. Leaving Central Park, you drift eastwards, taking 57th Street as far as 5th Avenue so you can dawdle to browse shop windows as you surreptitiously check for Dmitri behind you. Only when the coast is clear do you swing onto 6th Avenue to finally arrive at Rockefeller.
If, instead, you wanted to get to the corner of West 49th Street and 9th Avenue, you might leave Lincoln Center and head into Central Park, but once there you might immediately double-back on yourself to test Dmitri's training. (Experts will tell you that doubling-back on yourself is potentially confrontational, but nevertheless it remains one of the most favoured and most effective ways of evading a pursuer.) Once you had back-tracked a sufficient distance, you might take Columbus Avenue as far as West 54 Street but here veer east all the way to 8th Avenue before finally turning onto West 49th street. Figure 4 shows your route.
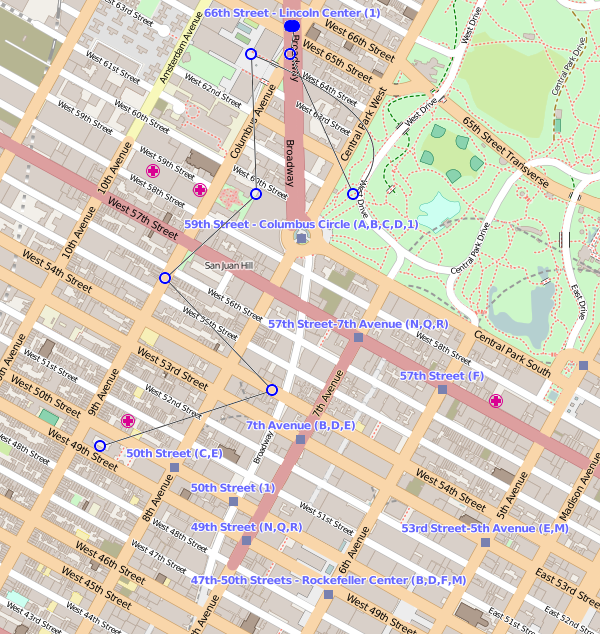
Figure 4: Another snaking path.
Even if you your destination were relatively close-by - in fact, especially so - you would still take wildly evasive maneuvers along the way. If you were going to San Juan Hill, just a few blocks away, you might (again) pop into Central Park first, exit all the way past 7th Avenue, double-back into Central Park (again!) and exit near Broadway before closing in on San Juan Hill. See figure 5.
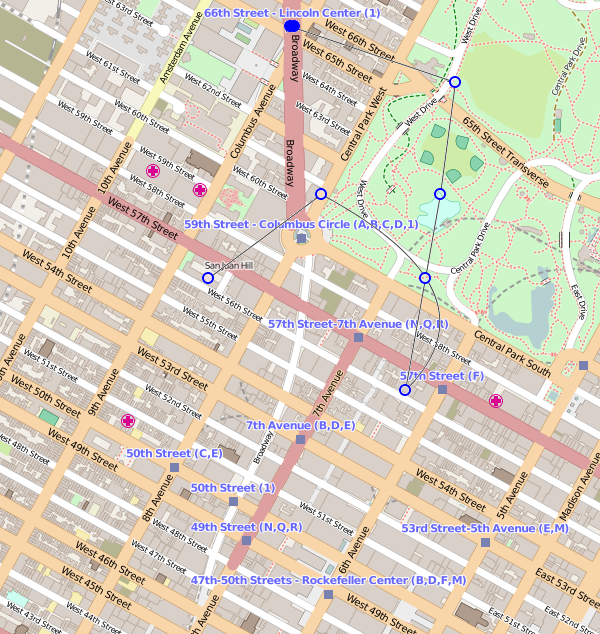
Figure 5: San Juan Hill.
The tremendously good news for you and your FBI colleagues is that this tiny section of New York offers thousands of ways of getting from the vicinity of Lincoln Center to Manhattan's many espionage-friendly locations. Not even Dmitri, with the unlimited resources of his nefarious international operation, could hope to surveil all these routes, all the time. See figure 6.
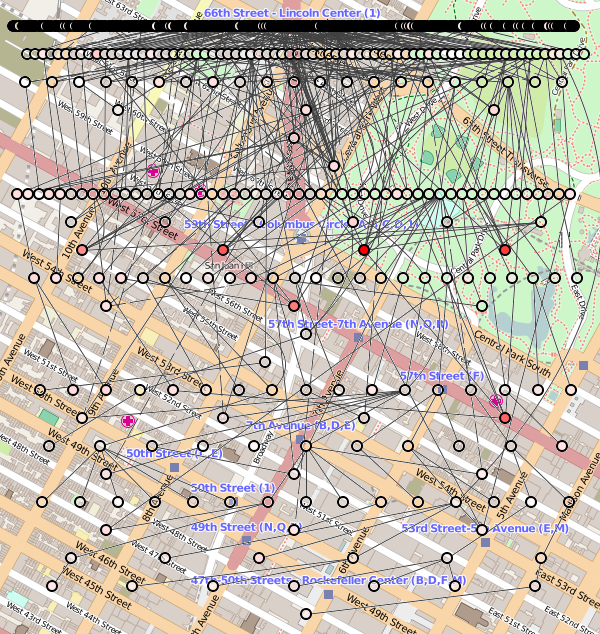
Figure 6: Good luck tracing all these paths.
But the tremendously bad news for software programmers is that they are Dmitri.
Not in spirit, of course, but they are Dmitri in that they need to keep track of every one of those paths in figure 6. For those paths in figure 6 are not, in fact, clandestine routes through New York but the transitive dependencies of methods within a single Java program. See figure 7.
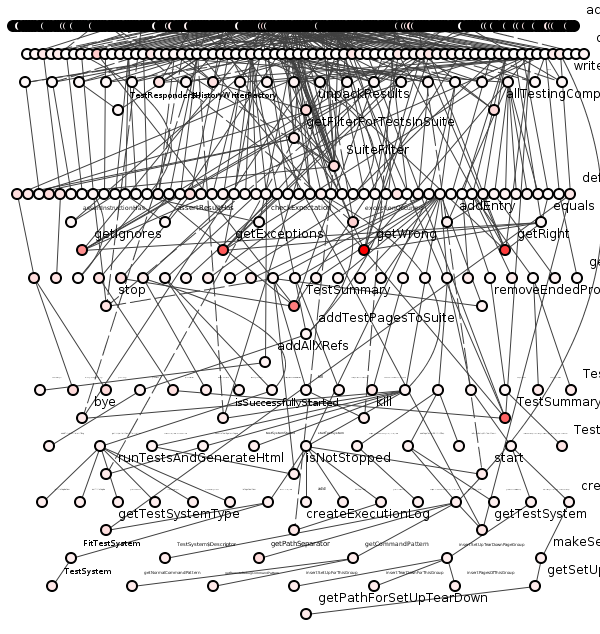
Figure 7: Package responders.run in FitNesse.
Worse still, figure 7 shows just those transitive dependencies within a single package of a program. Figure 8 shows the connections of the entire program.
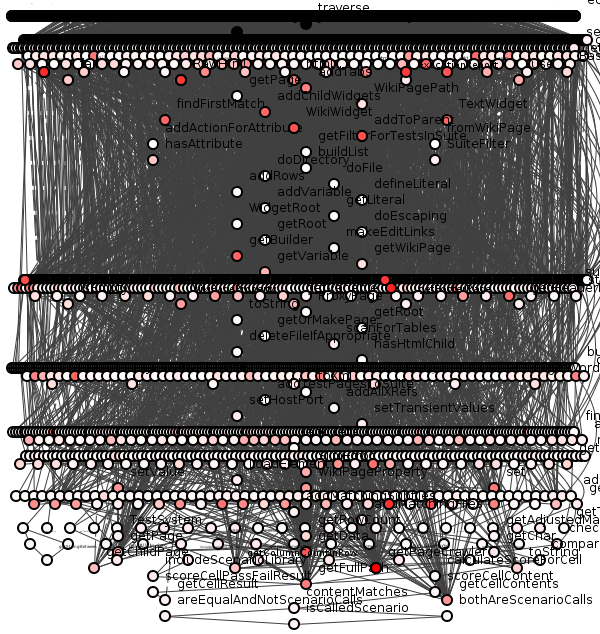
Figure 8: "All the dependencies."
And just as Dmitri would like to know the paths that the FBI take in going from A to B, so programmers need to know how methods relate to those on which they depend, however distantly, because only by understanding such connections can a programmer predict the cost of an update, in which a change to any method may ripple back to affect one or more dependent methods. Indeed, being able to predict such costs offers the very hallmark of a, "Well-structured," program.
Nevertheless, an FBI agent might look at figure 7 and wonder whose side the programmer was on. That agent might wonder why programmers create such deep program structures, so apparently designed to foil attempts at tracing transitive dependencies.
We need to create programs of such structural simplicity that would appall those vast FBI departments dedicated to finding ever more convoluted ways to cross populous urban areas.
And we need to start now.
Comrade.
Summary.
Sometimes the map is the territory.
Photo credit attribution.
New York map courtesy of OpenStreetMap.